

What is common between Uber, Airbnb, Tinder, and WhatsApp? Each of these successful companies has integrated their mobile applications into the core of their business operations. The mobile revolution has advanced to such an extent that mobile app development has become a key focus for enterprises across industries.
According to a report by , “Over 94% of the global internet population uses mobile phones to access the internet, and mobile devices account for over 58% of global website traffic.”. In this era of mobile connectivity, businesses must prioritize application security. Unlike websites and APIs, users interact deeply with mobile devices, entrusting them with a wealth of sensitive personal information.
Consequently, malicious hackers and fraudsters target mobile devices. Mobile application security has become a major concern for all companies, regardless of their target audience or market, as it directly affects stakeholder trust and loyalty.
However, the ever-increasing complexity and sophistication of mobile applications make it critical to choose the right tools for effective analytics. This blog post explores various tests and considerations for selecting the right mobile application security assessment tools, focusing on the pros and cons of each tool.
Mobile application security assessment is a process that evaluates a mobile application’s security posture to identify vulnerabilities, loopholes, and potential risks. The main objectives of a mobile application security assessment include:
1. Identifying vulnerabilities and weaknesses: Security assessment aims to identify potential risks that hackers might exploit. It thoroughly examines a mobile app’s architecture, code, and configuration, helping to proactively address vulnerabilities before exploitation.
2. Evaluating the effectiveness of security controls and measures: Security assessment analyzes the effectiveness of the implemented security controls within the mobile app. It ensures that encryption, authentication mechanisms, access controls, and other security measures are appropriately implemented and functioning as intended.
3. Mitigating risks associated with mobile app usage: Regular security assessment allows enterprises to identify and address potential risks associated with mobile apps. These risks include data breaches, unauthorized access, malware, and other threats that can compromise sensitive information.
Regularly assessing mobile app security is crucial in the enterprise environment for several reasons:
1. Adapting to the evolving threat landscape: The threat landscape is constantly evolving, with hackers continuously discovering new loopholes and techniques to exploit mobile apps. Regular security assessments allow businesses to stay ahead of potential threats and address emerging risks promptly.
2. Safeguarding sensitive data: Mobile apps often handle sensitive user data, such as personal information, payment details, and confidential business data. Assessing mobile app security helps protect this information from unauthorized access, data breaches, and other security incidents, preserving user trust and avoiding financial and reputational damages.
3. Meeting compliance requirements: Many industries have specific regulatory compliance requirements, such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS). Regular security assessments ensure mobile apps meet these standards, avoiding penalties and legal repercussions.

Common vulnerabilities and risks associated with mobile apps
Mobile apps are vulnerable to various risks and security concerns, including:
1. Insecure data storage: Improperly stored data, such as unencrypted user credentials or sensitive information stored in easily accessible locations, can be exploited by attackers.
2. Insecure communication: Inadequate encryption or the use of insecure protocols can expose sensitive data to interception, leading to data leakage or unauthorized access.
3. Poor authentication and authorization: Weak authentication mechanisms and improper authorization controls can allow unauthorized users to gain access to sensitive functionalities or data.
4. Code vulnerabilities: Flaws in the app’s code, such as buffer overflows, input validation issues, or insecure third-party libraries, can be exploited by attackers to gain control over the app or the underlying device.
5. Malware and malicious apps: Mobile apps can be infected with malware or disguised as legitimate apps. This can lead to privacy compromise, data theft, or unauthorized access.
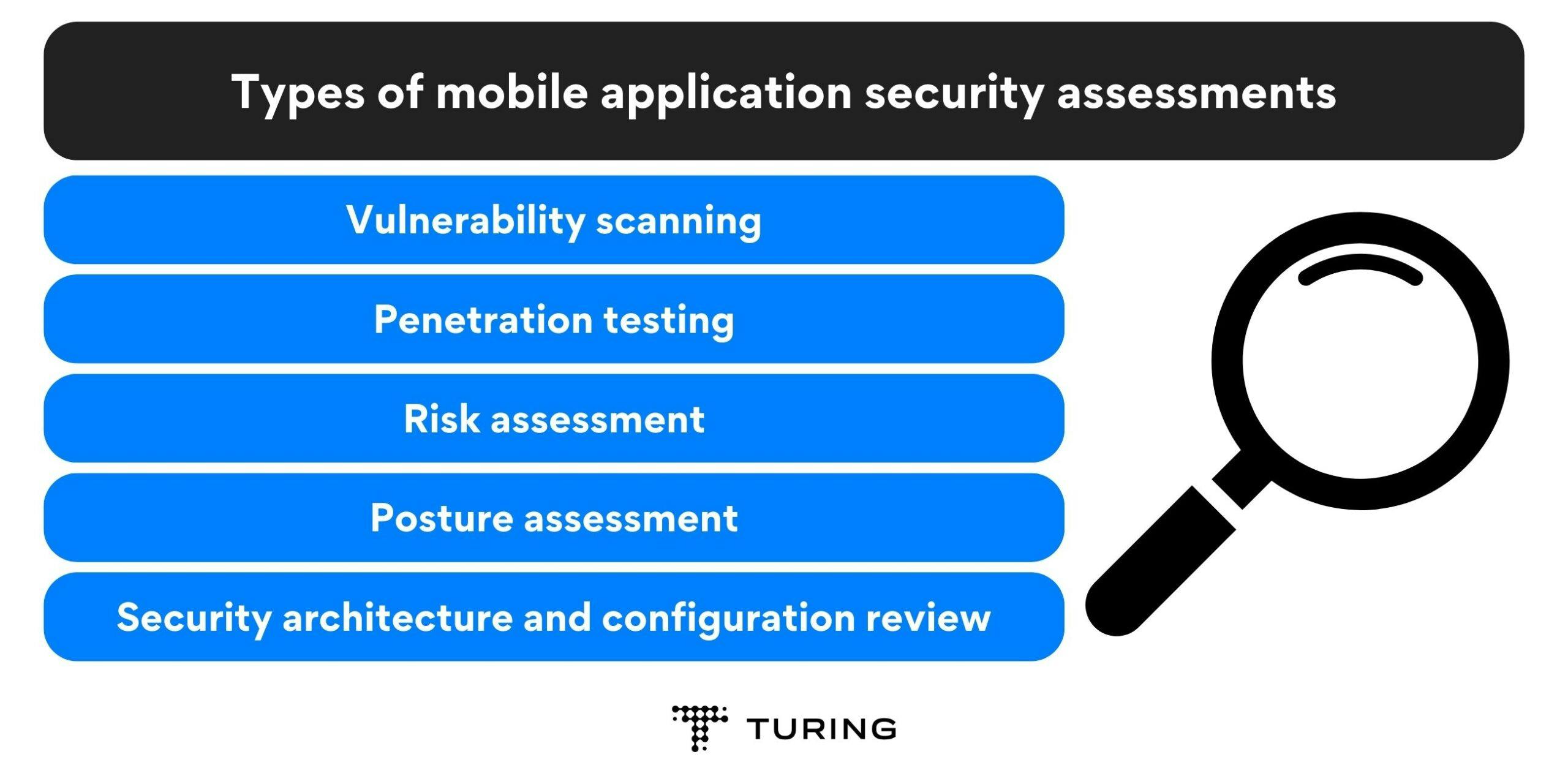
Types of mobile application security assessments
In this section, we will delve into various types of security tests specifically tailored for mobile applications. Let’s get started!
Vulnerability scanning utilizes automated tools to meticulously examine an app’s ecosystem for potential areas susceptible to compromise during an attack. These scanning tools diligently search for known vulnerabilities, particularly within software dependencies.
Moreover, vulnerability scanning excels at identifying easily overlooked loopholes by cross-referencing a comprehensive database of common vulnerabilities and their unique characteristics.
Once identified, the matches are promptly reported to the development team or the quality assurance (QA) team. Integrating vulnerability scans into a continuous integration (CI) pipeline can be an effective practice.
Penetration testing involves simulating attacks to assess an app’s security and pinpoint its weaknesses. This testing approach differs from vulnerability scanning as it incorporates human expertise, often through the involvement of an ethical hacker.These professionals use a range of techniques to breach an app’s defenses and identify potential areas that malicious attackers might exploit.
Unlike vulnerability scanning, which can occasionally generate false positives, the threats uncovered through penetration testing are genuine and provide a more precise understanding of the exact location of loopholes.
Risk assessment entails compiling a comprehensive inventory of all the components and individuals involved in an app’s ecosystem to identify their unique security risks in the event of a cyber attack.
Risk assessment aids in implementing targeted security measures for specific assets within an organization. It helps mitigate potential risks associated with insider threats, such as an IT department employee participating in or initiating an attack.
Posture assessment plays a crucial role in evaluating the current state of an app’s security. Developers can identify areas of improvement by conducting a thorough assessment.
Posture assessment also reveals what information may be compromised during an attack, the potential impact on business operations, the estimated recovery time, and the recommended preventive measures to implement.
Posture and risk assessments often complement each other and may incorporate other types of security testing. These comprehensive evaluations share a common objective: to identify security vulnerabilities, proactively prevent attacks, and effectively mitigate potential threats.
Security architecture review focuses on assessing the overall security architecture of the mobile app. It evaluates the effectiveness of security controls, encryption methods, data handling practices, and compliance with security standards.
On the other hand, configuration review ensures that the configurations of external services and APIs are properly implemented, minimizing the risk of unauthorized access or data leakage.
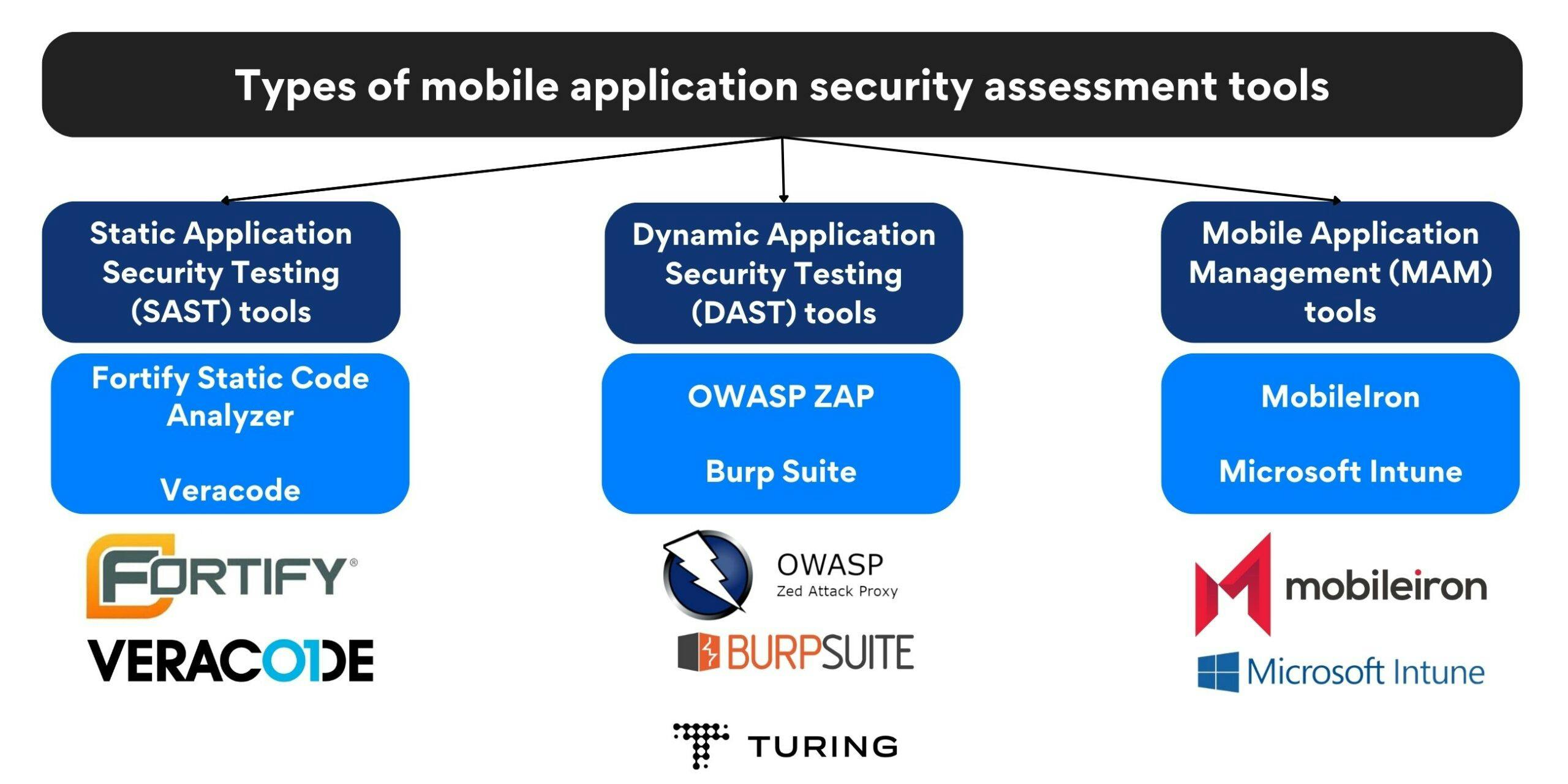
Types of mobile application security assessment tools
Mobile application security assessment tools identify security threats and ensure the robustness of mobile applications. In this section, we will explore three types of mobile application security assessment tools that every enterprise should consider:
SAST tools are designed to identify vulnerabilities in mobile applications during the development phase. They analyze the source code or compiled versions of the application to uncover potential security flaws. SAST tools offer several benefits, such as early detection of vulnerabilities, improved code quality, and reduced development costs by addressing issues at an early stage.
Some popular SAST tools include:
Dynamic application security testing (DAST) tools
DAST tools evaluate the security of mobile applications in real time by simulating attacks and monitoring their responses. These tools analyze the application’s behavior and interactions with external systems to identify potential vulnerabilities. DAST tools are particularly effective in detecting issues that can only be identified during runtime.
Some popular DAST tools include:
MAM tools focus on managing and securing mobile applications deployed within an enterprise environment. These tools enable businesses to enforce security policies, control access to sensitive data, and remotely manage applications on employees’ devices. MAM tools provide essential benefits like enhanced data protection, centralized app distribution, and improved compliance management.
Some popular MAM tools include:

List of top mobile app security assessment tools
Modern-day enterprises need reliable mobile app security testing tools to protect their applications from potential cyberattacks and data breaches. Some of the top mobile app security assessment tools that can assist enterprises in fortifying their mobile app security include:
QARK (Quick Android Review Kit) is an open-source tool that focuses on identifying security vulnerabilities in Android applications. QARK offers a user-friendly interface and generates detailed reports, making it a valuable tool for enterprises. Its key features include:
Pros of QARK:
Cons of QARK:
Data Theorem is a comprehensive mobile app security testing tool that covers both Android and iOS applications. It offers static and dynamic analysis, vulnerability assessment, and compliance testing. While Data Theorem provides advanced security testing capabilities, its premium features may come with a higher price tag. Its key features include:
Pros of Data Theorem:
Cons of Data Theorem:
App-Ray is a versatile mobile app security testing tool that supports iOS, Android, and Windows phone platforms. Its key features include:
Pros of App-Ray:
Cons of App-Ray:
Checkmarx is a popular mobile app security testing tool that focuses on identifying and remediating code vulnerabilities. Its key features include:
Pros of Checkmarx:
Cons of Checkmarx:
NowSecure is a mobile app security testing tool that focuses on both iOS and Android platforms. Its key features include:
Pros of NowSecure:
Cons of NowSecure:
Appknox is a cloud-based mobile app security testing tool that supports both iOS and Android platforms. Its key features include:
Pros of Appknox:
Cons of Appknox:
Fortify on Demand is a cloud-based mobile app security testing tool provided by Micro Focus. Its key features include:
Pros of Fortify on Demand:
Cons of Fortify on Demand:
HCL AppScan is an enterprise-grade mobile app security testing tool that supports iOS and Android platforms. Its key features include:
Pros of HCL AppScan:
Cons of HCL AppScan:
AppSweep is a cloud-based mobile app security testing tool that supports both iOS and Android platforms. Its key features include:
Pros of AppSweep:
Cons of AppSweep:
Veracode is an enterprise-grade mobile app security testing tool that supports both iOS and Android platforms. Its key features include:
Pros of Veracode:
Cons of Veracode:
Synopsys is a comprehensive mobile app security testing tool that supports iOS, Android, and Windows Phone platforms. Its key features include:
Pros of Synopsys:
Cons of Synopsys:
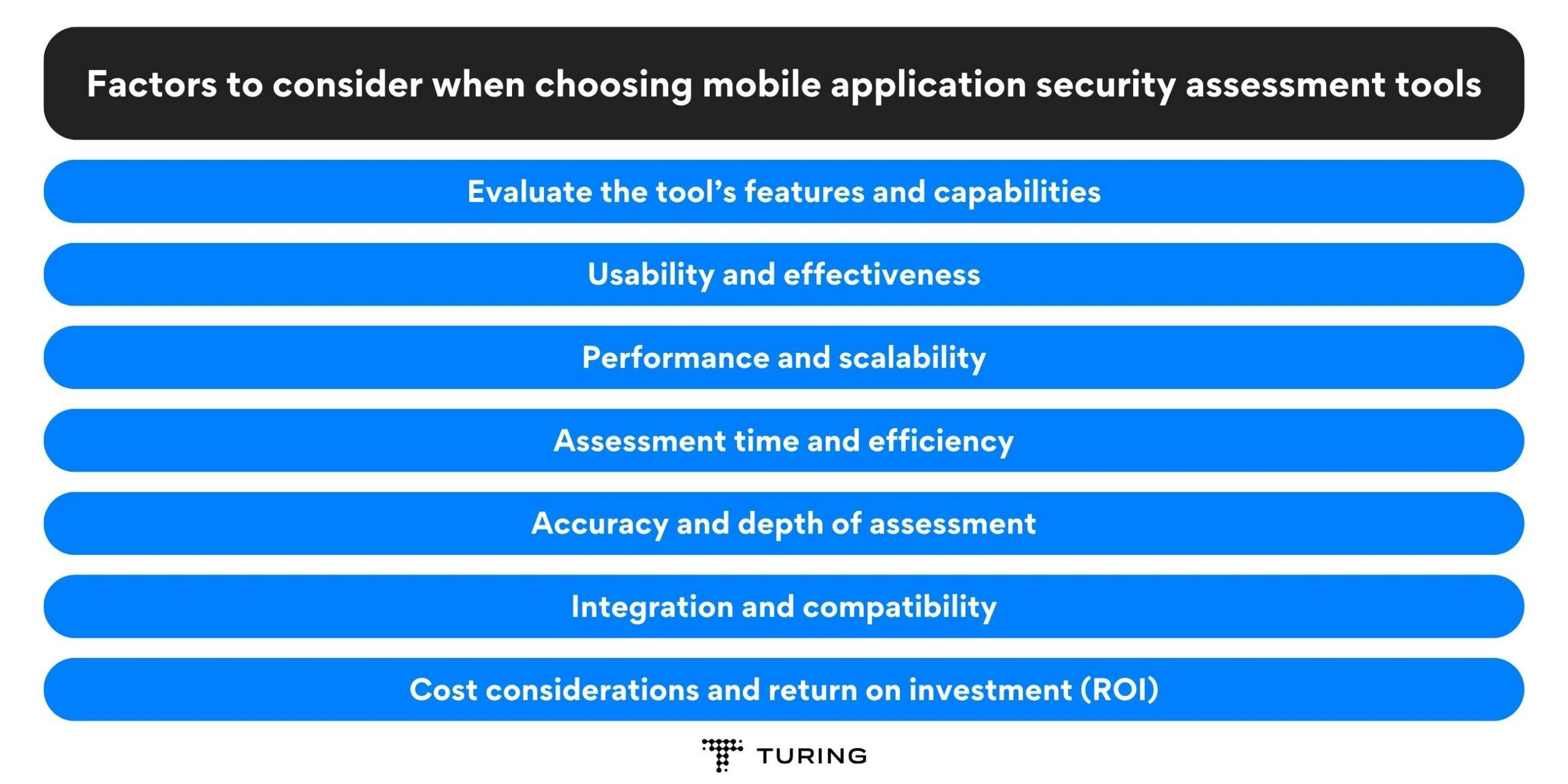
Factors to consider when choosing mobile application security assessment tools
In this section, we will discuss the key factors enterprises should consider when choosing mobile application security assessment tools. Let’s dive in!
Start by evaluating the tool’s compatibility with various mobile platforms such as iOS and Android. A comprehensive security assessment tool should be able to test applications across different platforms to ensure consistent protection.
Additionally, look for features essential for effective security testing, such as dynamic analysis, static analysis, code review, and penetration testing capabilities. The tool should also support the testing of both native and hybrid applications.
While evaluating security assessment tools, usability and effectiveness should be critical factors. A tool may have advanced features, but if it is complex and hard to use, it can reduce your security team’s efficiency.
Look for tools with intuitive user interfaces that provide clear instructions and guidance. Consider the learning curve associated with the tool and the availability of comprehensive documentation or support to ensure smooth adoption and maximum effectiveness.
For enterprises dealing with a large number of mobile applications, the performance and scalability of the assessment tool are paramount. The chosen tool should be able to handle large-scale assessments without compromising the accuracy and speed of the process.
The tool should not impact the performance of the mobile applications under assessment. Test the tool’s ability to handle a high volume of tests and verify if it can efficiently scale as your organization’s mobile application portfolio grows.
Time is money when it comes to security assessments. Look for tools that can conduct assessments quickly and efficiently. Automation capabilities can significantly streamline the assessment process, allowing security teams to focus on analyzing and addressing vulnerabilities rather than spending excessive time on manual tasks.
Evaluate the tool’s speed and efficiency in identifying and reporting threats and loopholes to ensure that it meets your organization’s time constraints.
The primary purpose of a mobile application security assessment tool is to identify vulnerabilities accurately. Assess the tool’s ability to detect various types of vulnerabilities, including common ones like insecure data storage, improper session handling, and insecure communication.
A good tool should provide detailed reports with actionable insights, enabling your security team to prioritize and address the identified risks effectively.
Consider the tool’s compatibility with your existing security systems or frameworks. Integration capabilities with other security tools, such as vulnerability scanners or incident response platforms, can enhance the overall security posture of your organization.
Additionally, ensure that the tool supports the mobile platforms your organization uses, ensuring comprehensive coverage across different operating systems and versions.
Cost is an important factor for any organization. Evaluate the costs associated with different mobile application security assessment tools, including licensing fees, maintenance costs, and any additional expenses. However, it’s crucial to balance cost considerations with the potential return on investment (ROI).
Investing in robust security assessment tools can help prevent data breaches, financial losses, and damage to your organization’s reputation, making it a worthwhile investment in the long run.
In conclusion, it is important to assess which tool is most suitable for your mobile application. Choosing the right tool depends on the specific requirements of your mobile application and the desired level of security assessment.
Mobile application security assessment tools are likely to evolve further to keep pace with the ever-changing threat landscape. We can expect enhanced automation capabilities, improved integration with development workflows, more advanced vulnerability detection techniques, and better support for emerging mobile platforms.
Additionally, tools may increasingly incorporate artificial intelligence and machine learning algorithms to identify and address vulnerabilities more accurately and efficiently.
In enterprise environments, mobile application security assessment tools will continue to play a vital role in maintaining the security and integrity of mobile apps. As mobile technology advances and threats become more sophisticated, enterprises must adapt by leveraging reliable and comprehensive security assessment tools to safeguard their mobile applications, protect sensitive data, comply with regulations, and preserve user trust.
Turing’s mobile app development services can help assess and enhance the security of mobile apps and allow organizations to stay ahead of potential threats and ensure a secure mobile environment for their stakeholders.
Aditya is a content writer with 5+ years of experience writing for various industries including Marketing, SaaS, B2B, IT, and Edtech among others. You can find him watching anime or playing games when he’s not writing.
By clicking Subscribe you're confirming that you agree with our Terms and Conditions